Business Needs & Use Cases
Every organization has unique operational demands, regulatory pressures, and growth objectives. Our approach starts with understanding business needs and translating them into practical, scalable technology solutions that support real-world use cases.
Schedule A Meeting
Need A Reliable 24/7 Managed Services Provider ?
Cloud Solutions for Enterprise
Enterprise cloud adoption requires more than migration — it demands control, security, scalability, and governance. Our Cloud Solutions for Enterprise help organizations design, operate, and optimize cloud environments that support complex workloads, regulatory requirements, and long-term growth. We deliver cloud solutions that are architected for resilience, cost efficiency, and operational clarity, across public, private, and hybrid models.
99.95%
Cloud service availability target


Enterprise Cloud Architecture
Design secure, scalable cloud architectures aligned with business objectives and operational requirements.
Hybrid & Multi-Cloud Solutions
Integrate on-premises environments with public and private cloud platforms for flexibility and resilience.
Cloud Migration & Workload Optimization
Plan and execute phased migrations while optimizing performance and resource utilization.
Security & Identity Integration
Embed identity, access control, encryption, and security monitoring into cloud environments.
Cost Management & Optimization
Implement governance and cost controls to manage spend, improve efficiency, and prevent waste.
Operational Management & Governance
Provide monitoring, policy enforcement, documentation, and ongoing operational support.
Why Our Approad Works
We approach enterprise cloud as a long-term operational platform, not a short-term project. Every solution is designed to be secure, auditable, and manageable, ensuring IT teams retain visibility and control as environments scale. By aligning cloud architecture with governance and managed operations, we help enterprises reduce risk, improve agility, and support continuous innovation.

Scalable and resilient cloud infrastructure

Controlled costs and predictable operations

Security and compliance by design

Cloud environments built to scale

Seamless integration with existing systems

Law Firm Cyber Resilience

Book a cloud assessment to evaluate your environment and define a secure, scalable cloud strategy.


Remote Work Management
Modern workforces are distributed, mobile, and constantly connected. Our Remote Work Management solutions enable organizations to provide secure, reliable, and productive digital workspaces for employees — regardless of location. We design and manage remote work environments that balance user experience, security, and compliance, ensuring teams can work effectively without increasing risk or operational complexity.
What We Deliver
-
Secure Digital Workspace Design
Create centralized, secure workspaces that provide access to applications, data, and collaboration tools. -
Identity & Access Control for Remote Users
Enforce strong authentication, conditional access, and least-privilege policies for remote and hybrid staff. -
Device Management & Compliance
Manage and secure corporate and BYOD devices to ensure they meet security and compliance standards. -
Collaboration & Communication Enablement
Deploy and manage collaboration platforms that support messaging, meetings, and file sharing. -
Performance, Availability & User Support
Monitor remote access performance and provide responsive support to minimize downtime. -
Security Monitoring & Risk Management
Detect and respond to remote access threats, suspicious behavior, and policy violations.
Key Outcomes
-
Secure and consistent remote access
Standardized identity and access controls provide secure, reliable connectivity across all remote users. -
Improved employee productivity and experience
Streamlined access and stable systems reduce friction and support efficient day-to-day work. -
Reduced security exposure from remote endpoints
Centralized endpoint management and security policies minimize risks introduced by remote devices. -
Centralized management and visibility
Unified tools provide clear visibility into users, devices, access, and security posture. -
A Strategy Built on Control, Not Complexity
Streamlined access and stable systems reduce friction and support efficient day-to-day work. -
Scalable remote work infrastructure
Remote work platforms are designed to scale as workforce size and business needs evolve.
Why Our Approach Works
We treat remote work as an operational and security discipline, not just a set of tools. Our solutions integrate identity, endpoint security, and centralized management to maintain visibility and control across distributed teams. By standardizing remote work environments, we help organizations reduce risk, improve productivity, and support flexible working models at scale.
M&A Tech Integration
Mergers and acquisitions introduce significant technology risk if not managed correctly. Our M&A Tech Integration solutions help organizations rapidly and securely integrate IT environments, ensuring business continuity, security, and operational alignment from day one. We support organizations through every phase of the integration — from due diligence to post-merger optimization — minimizing disruption while enabling scale.
100%
Unified identity and access coverage across merged environments


IT Due Diligence & Risk Assessment
Assess infrastructure, security posture, applications, and technical debt to identify risks before integration.
Integration Strategy & Roadmap
Define clear integration plans covering identity, infrastructure, applications, and data.
Identity & Access Consolidation
Unify user identities, access controls, and authentication across merged environments.
Infrastructure & Application Integration
Consolidate or integrate networks, cloud platforms, servers, and business applications.
Security & Compliance Alignment
Align security controls, policies, and compliance standards across organizations.
Post-Merger Optimization & Stabilization
Optimize performance, costs, and operations after initial integration is complete.
Why Our Approad Works
We treat M&A integration as both a technical and operational challenge. Our structured approach reduces uncertainty, accelerates timelines, and ensures systems remain secure and supportable throughout the transition. By focusing on governance, documentation, and controlled execution, we help organizations unlock value from acquisitions without increasing long-term complexity or risk.

Faster, Lower-Risk Integrations

Minimal Business Disruption

Unified Security and Access Control

Clear Visibility and Governance Post-Merger

Optimized and Scalable IT Environments
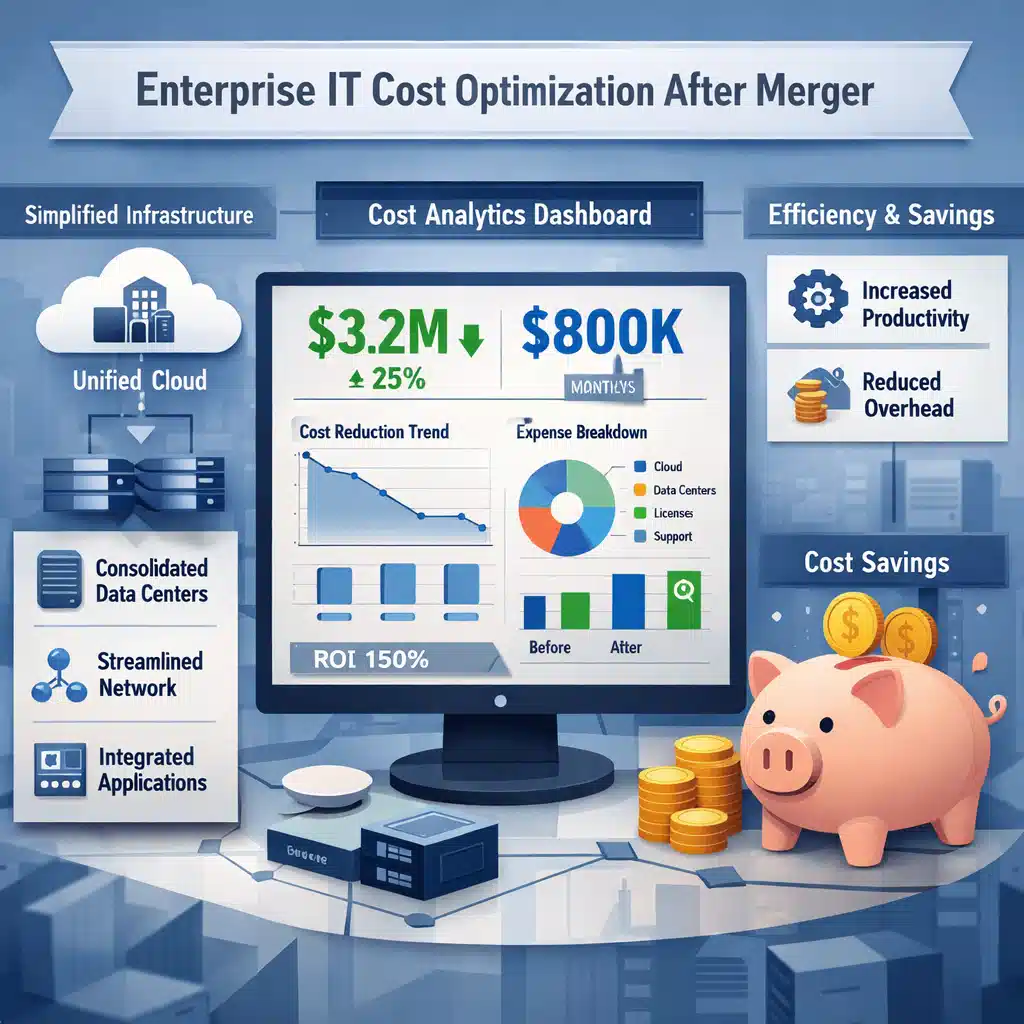
Cost Transparency and Operational Efficiency

Book an M&A technology assessment to plan a secure and efficient integration strategy.
Legacy Modernization
Legacy systems can limit agility, increase risk, and drive up operational costs. Our Legacy Modernization solutions help organizations transform aging infrastructure and applications into secure, scalable, and maintainable platforms — without disrupting business operations. We take a phased, risk-managed approach to modernization, ensuring continuity while enabling long-term innovation.
What We Deliver
-
Legacy Environment Assessment
Evaluate infrastructure, applications, dependencies, performance, and security risks. -
Modernization Strategy & Roadmap
Define phased modernization plans aligned with business priorities and risk tolerance. -
Application Refactoring & Migration
Modernize applications through refactoring, re-platforming, or migration to modern environments. -
Infrastructure Transformation
Replace legacy hardware and operating systems with virtualized, cloud, or hybrid platforms. -
Security & Compliance Enhancement
Strengthen security controls and align legacy systems with modern compliance standards. -
Operational Stabilization & Optimization
Improve performance, reliability, and manageability after modernization.
Key Outcomes
-
Reduced technical debt and operational risk
Legacy systems and duplicated platforms are rationalized to reduce complexity, instability, and integration risk. -
Improved performance and system reliability
Consolidated architectures improve system responsiveness, uptime, and operational consistency across environments. -
Enhanced security and compliance posture
Unified security controls and policies strengthen protection and ensure consistent compliance across systems. -
Lower maintenance and support costs
Standardized platforms reduce ongoing support effort, licensing overhead, and operational maintenance costs. -
Scalable platforms ready for future innovation
Modernized environments enable controlled scaling and faster adoption of new technologies and capabilities.
Why Our Approach Works
We modernize with business continuity in mind. Rather than forcing disruptive change, we carefully sequence upgrades, migrations, and integrations to minimize downtime and operational risk. By combining technical expertise with structured governance, we help organizations reduce technical debt while building platforms that are ready for future growth.
Compliance Automation
Regulatory compliance is increasingly complex, time-consuming, and resource-intensive when managed manually. Our Compliance Automation solutions help organizations continuously meet regulatory and security requirements through automated controls, monitoring, and reporting. We replace manual, reactive compliance processes with automated, auditable, and repeatable workflows that reduce risk while improving operational efficiency.
100%
Mapped regulatory controls with continuous compliance visibility


Compliance Framework Mapping
Map regulatory and security requirements to technical controls across systems, cloud platforms, and endpoints.
Policy Enforcement & Automated Controls
Implement automated policies for identity, access, data protection, and configuration compliance.
Continuous Monitoring & Alerts
Monitor compliance status in real time and alert teams to deviations or risks.
Audit Readiness & Evidence Collection
Automate evidence gathering, reporting, and documentation to support audits and reviews.
Risk & Exception Management
Track risks, exceptions, and remediation actions with clear ownership and timelines.
Compliance Reporting & Visibility
Deliver executive and technical reporting to demonstrate compliance posture and trends.
Why Our Approad Works
We treat compliance as an operational discipline, not a periodic exercise. By embedding compliance controls into everyday IT operations, we help organizations stay continuously audit-ready without disrupting productivity. Our automation-driven approach reduces human error, improves consistency, and provides leadership with clear visibility into compliance posture at all times.

Continuous, real-time compliance

Reduced audit preparation effort

Lower regulatory and security risk

Improved governance and accountability

Scalable compliance processes

Consistent Policy Enforcement


Disaster Recovery
Unexpected disruptions — whether cyber incidents, system failures, or natural events — can bring operations to a halt. Our Disaster Recovery solutions ensure your business can recover quickly, safely, and predictably, minimizing downtime and data loss. We design, implement, and manage disaster recovery strategies that protect critical systems, maintain business continuity, and support regulatory requirements.
What We Deliver
-
Business Impact & Risk Assessment
Identify critical systems, recovery priorities, and acceptable recovery time and data loss thresholds. -
Disaster Recovery Strategy & Design
Define recovery architectures aligned with business objectives, including on-premises, cloud, and hybrid models. -
Backup, Replication & Failover
Implement secure backup, data replication, and automated failover to ensure system availability. -
Recovery Testing & Validation
Perform regular testing and simulations to validate recovery plans and readiness. -
Security & Compliance Alignment
Ensure recovery processes meet security, data protection, and regulatory requirements. -
Ongoing Management & Optimization
Continuously monitor, maintain, and improve disaster recovery capabilities.
Key Outcomes
-
Reduced downtime and data loss
Recovery strategies minimize service interruption and prevent loss of critical business data. -
Clear recovery objectives and processes
Defined recovery time and recovery point objectives guide consistent and predictable recovery actions. -
Tested and reliable recovery plans
Regular testing ensures recovery procedures work as intended during real incidents. -
Improved resilience and business continuity
Systems are designed to withstand disruptions and maintain essential business operations. -
Confidence during critical incidents
Teams can respond quickly and decisively with proven recovery processes in place.
Why Our Approach Works
We focus on predictable recovery, not just backup. Every disaster recovery solution is designed with clear objectives, documented procedures, and tested execution. By integrating disaster recovery into everyday IT operations, we help organizations maintain resilience, protect data, and respond confidently to unexpected events.

